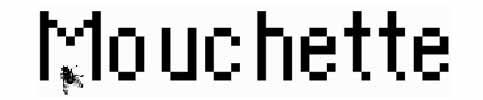Networks of Care
Networks of care
In 2011, I curated NetArtWorks, a series of small thematic online net art exhibitions on the theme of Identity Works for SKOR (Foundation for Art and Public Domain) in Amsterdam. Each presentation consisted of two newly commissioned artworks in combination with an existing iconic artwork. mouchette.org (1996) by Martine Neddam fit the theme perfectly.1 mouchette.org is an interactive website that started in 1996 and has evolved over the years. The exhibition on SKOR’s website raised several issues that I discussed with Neddam. Would mouchette.org be mirrored or embedded in SKOR, or should screen capture videos of different people navigating the site be shown? How should the biography of the work be presented? Many of these discussions were directed toward the old aesthetics of the site, and consequently developed into discussions on the conservation of mouchette.org. For example, features that were largely unknown in 1996 are widely used today, which makes many of the aesthetics seem outdated. The most obvious example is the entry page, which has early HTML checkboxes that are no longer used. Another example is the ‘blog’-like structure used in some of the projects. Whereas in 1996 the site would be referred to as a diary or personal website, today it is understood as a blog even though it is quite different from one. Nonetheless, will people 30 years from now understand the meaning of the word ‘blog’, or for that matter a ‘personal website’? Similarly, some of the interactive elements on the website are antiquated and difficult to explain without becoming overly technical or historical.
Instead of incorporating the old artwork into SKOR, Neddam proposed to concentrate on making a new work, a physical translation of the online project, focusing on the identity, or the brand, of mouchette.org. This led to the creation of the Guerrilla Fanshop. The shop sold some objects that were part of old projects, but allowed for a distinctive appearance: mimicking typical fan gear and paraphernalia such as stickers, T-shirts and bracelets. The Guerrilla Fanshop could be visited in SKOR’s exhibition space, a small semi-detached building with its own entrance and two large windows overlooking the street. The exhibition space shared many of the characteristics of mouchette.org – a single entity in a larger infrastructure that could be changed according to specific ‘rules’ – and it became an interesting metaphor for the work. Similarly, the Guerrilla Fanshop was symbolic: on the one hand it reflected the desires of 13-year-old girls, while on the other, in light of our discussions, Neddam would like the conservation of a work of art to become a new work of art.2 The suggestion to conserve mouchette.org by creating a new work required Neddam to re-use and re-stage specific parts of the collection that consists of both online and offline artworks. In this way, an ‘archive is never the “freezing” of something’.3 Rather it surpasses the documented – or still existing – works to produce and proliferate new works.
Neddam’s suggestions seem far removed from conventional conservation practices. The theory and practice of conservation usually starts with addressing the issue of how culturally significant works can be conserved to their authentic state or as close as possible? Or, if needed, how can artefacts, like art, be restored to their authentic states by means of intervention? When considering the notion of variability, mouchette.org is an interesting case to explore, because it is presented in various constellations and forms while maintaining many of its existing elements. In other words, in order for mouchette.org to ‘survive FOREVER’ as a mix of new and existing parts, it is necessary to find a way to conserve at least parts of the work for future re-creation. In this chapter I focus on the possibility of conserving mouchette.org by assessing if and how a net artwork can be conserved. I also take into consideration the specific knowledge that is needed to conserve artworks that continually change. First of all, what does authenticity mean in conservation, and what is its value and meaning in relation to variability?
Authenticity
The question of authenticity is a recurring topic and one of the key concepts in conservation theory. Nevertheless, for many decades the meaning of authenticity did not receive critical attention. The concept of authenticity was first given credence in the Venice Charter of 1964, which stated in part that ‘the common responsibility to safeguard [ancient monuments] for future generations is recognized. It is our duty to hand them on in the full richness of their authenticity’ (ICOMOS 1965). Most likely due to the homogenous group of discussants the term itself was taken for granted (Stovel 1995). Thirty years later, the International Council on Monuments and Sites (ICOMOS), together with the International Centre for the Study of the Preservation and Restoration of Cultural Property (ICCROM) and the United Nations Educational, Scientific and Cultural Organization (UNESCO), organized ‘The Nara Conference on Authenticity’ in Japan. Representatives from 28 countries discussed the many complex issues associated with defining and assessing authenticity. The outcome was the Nara Document on Authenticity (Larsen 1995), which built on the Venice Charter. This time the concept stressed the particular importance and application of authenticity as it relates to cultural heritage, as well as how authenticity is rooted in specific cultural contexts and thus should be considered accordingly (Larsen 1995). Yet, over the years the exact meaning of authenticity has been contested and it is still subject to critical revision, reinvestment and redirection. This makes authenticity a variable concept.4
In art conservation, authenticity is generally used to measure the originality of materials and an artwork’s completeness (Laurenson 2006). For museums, the quest for authenticity is important because it represents ‘the real objects, the actual evidence, the true data as we should say, upon which in the last analysis the materialistic meta-narratives depend for their verification’ (Pearce 1992:4). This means that measuring authenticity allows for a distinction between ‘real’ works and forgeries. Elizabeth Pye, Professor of Archaeological & Museum Conservation, proposed a working definition that has been adopted by many conservators:
Authenticity has been generally considered to mean genuine in terms of materials, workmanship and date, and processes used to authenticate objects concentrated on the identification of raw materials, the examination of tool marks and other aspects of construction, and, where possible, the use of scientific dating techniques.
(2001:59)
In conservation theory this type of authenticity is also referred to as nominal authenticity, which defines empirical data, or ‘the correct identification of the origins, authorship, or provenance of an object, ensuring, as the term implies, that an object of aesthetic experience is properly named’ (Dutton 2003:259). Philosopher Dennis Dutton distinguishes nominal authenticity from expressive authenticity, which is seen as a ‘committed, personal expression’ in which the artist (or performer) is faithful to his/her own artistic style and creative process, rather than to a historical tradition (Dutton 2003:267). Whereas nominal authenticity enables an understanding of the practice and history of art through material analysis, expressive authenticitymanifests itself through individual and/or collective values, beliefs and ideals. These are merely two types; essentially, authenticity has been approached and defined in multiple ways, particularly under the influence of less stable artworks and an increasing understanding of technical artworks in the last two decades.5
It could be argued that the ease and tolerance of replication, appropriation and versioning in the World Wide Web further complicates authenticity. Although artists have employed these strategies for many decades, the speed and accessibility of the network means that visuals, videos and sounds can be readily transferred and copied within seconds. Walter Benjamin’s influential article ‘The Work of Art in the Age of Mechanical Reproduction’ (1969[1936]) is still the most cited when discussing the question of authenticity in relation to art produced by technical means. He asserts that reproducibility cannot be authentic because the ‘aura’ of the original work is lost. According to Benjamin, the manipulability or malleability of the photographic or phonographic copy diminishes what is at the crux of authenticity, ‘the authority of the object’. This is due to the loss of its presence in time and space (Benjamin 1969:521). Net artworks are for the most part inherently variable and oftentimes multiple versions of the artwork exist. However, this does not equal reproduction; these are different versions, hence they can still be authentic. mouchette.org is exemplary in this sense. The work is rooted in specific art historical and technical contexts. The different projects act like an assemblage that evolves; in addition, the deliberately ambiguous wordplays and references influence authenticity in a way that questions both nominal (material) and expressive qualities (conceptual ideas).
mouchette.org
mouchette.org is an interactive website created in 1996 by a pseudonymous character initially known as Mouchette. The project developed and evolved over the years. Additional pages were added and other physical offline projects and events were organized. In 2010, after many years of well-kept secrecy, Martine Neddam revealed herself as the author behind Mouchette.6 However, most people doubted her real identity since Neddam had performed role-plays several times before. For example, when asked to present mouchette.org at an event, she asked other people to stand in as Mouchette (Dekker 2011a).7 Nevertheless, even today the visitor is welcomed on the homepage by a large bright flower, with a few red drops, a fly buzzing, some ants squirting around and a small stamp-size photo in the upper left-hand corner of a young girl looking down, presumably Mouchette (Figure 3.1). There are several checkboxes and a drop-down menu from which several projects can be accessed, and unexpectedly one can stumble upon invisible links that direct to a project or present a pop-up text. In the background one can hear the howling sound of a wolf, or, when revisiting the site, the soft sobbing, giggling or yawning of a girl, or merely a brief ‘bonjour’. Mouchette claims to be almost 13 years old, an artist and living in Amsterdam. What initially appears to be the personal website, in English and French, of a female teenager evolves into darker themes in subsequent pages.
The name Mouchette derives from the novel Nouvelle histoire de Mouchette (1937) by French author Georges Bernanos, and the film Mouchette(1967) by Robert Bresson, a free adaptation of the novel. In both accounts, Mouchette is a girl between childhood and adolescence. She leads a harsh life: rejected by society (family, school and friends), raped by a trusted older man, and the death of her mother. These events leave her disheartened, and although never made explicit, the story ends with her suicide. Bernanos claims that the story was inspired by his first-hand accounts of the atrocities of the Spanish Civil War while he was exiled in Majorca. Bresson wanted viewers to understand how humans negotiate their own redemption (Hudson 2009). mouchette.org takes many of the themes that play out in the book and film and re-performs them in a contemporary setting, namely as an online diary with several project pages. Neddam uses some Web characteristics in intricate ways to emphasize the drama and enigma of the story. For example, hyperlinks create confusing circulation; interactive possibilities produce several layers of information and identity play is performed in various ways. The latter is best visible in the wordplay of ‘mouchette’, the website’s domain name, the girl’s name and the French word for ‘little fly’, but is differently shaped in subsequent projects. The equivocal use of these characteristics makes it difficult to comprehend and identify important and less relevant aspects of the project. Moreover, the themes and concepts used in mouchette.org amplify this sense of ambiguity.
For example, the website’s most prominent themes evolve around metaphors of violence and death, more specifically suicide.8 On the opening page, a large flower with several small drops of blood on its petals accompanies the photo of Mouchette. An animated GIF9 of a fly moves slowly in the centre of the page, while two animated GIFs of ants move frantically to-and-fro at the edge of the screen.10 This somewhat weird scene is enhanced by a female moaning softly, almost sexually. When clicking on the fly, the visitor enters a page where Mouchette points to a sentence with the meaning of her name. Another click on the fly opens a new page with a half-finished meal on a dinner plate. The image is abstract and shows a hand pecking at the remains.11 Another hand becomes visible when scrolling down. This project can also be accessed by clicking on ‘dead fly’ in the drop-down menu on the homepage. A grey square with the words ‘it’s me’ circles above the plate, accompanied by the sound of a buzzing fly. Clicking on the square proves rather difficult. It is either through determination or smart thinking that the button is ‘caught’. If successful, a black page opens. Green letters appear after a few seconds, as if typed live. They accuse the visitor of killing the fly when he/she pressed the button on the previous page. The fun of play on the previous page is turned into dark humour. The story continues when the fly – or the girl? – asks the visitor to tell her why she’s dead. An e-mail entry opens, and when clicked again (either by ignoring or sending a message), another page opens with Lullaby for a Dead Fly. The dark, almost melancholic, tonal music accompanies fragments of text that pass across the screen from all sides. The text consists of changing e-mails sent by people who have answered the question.
As mentioned, over the years Neddam was invited to present the project at exhibitions and events, but instead of showing up herself she asked other people to impersonate Mouchette. In some instances a 13-year-old girl presented the project’s website, in others, a male in his 30s. Neddam also used various objects in exhibitions, from videos to cheap and colourful soft toys, post cards and compact discs (Figure 3.2). She also organized several events around the website, for example, a Last Birthday Party (14 December 2001) and the Guerrilla Fanshop (6 July – 26 August 2011) (Figure 3.3). Neddam considers all of these outputs to be integral elements of mouchette.org. As such, Mouchette can be seen as an identity through which various projects are presented, or as Neddam calls it a ‘brand’ (Dekker 2011a). Use of the terms ‘brand/branding’ are interesting when considered in the light of the readings of sociologist Celia Lury, who argues that a brand is ‘a platform for the patterning of activity, a mode of organizing activities in time and space’ (2004:1).12 This means that a brand emerges in parts. Therefore, as she argues, it is an open system that extends into, or implicates, social relations. Furthermore, ‘it is some-thing that is identifiable in its doing’ (ibid.).13 This notion of ‘brand’ affirms the construction of mouchette.org as an assemblage that varies over time and is composed of different parts and projects. The suggestion of an assemblage is reinforced by the intricate navigation of the website, which changes with each visit. The multiple projects both signify and give meaning to Neddam’s Mouchette. Arguably, these characteristics are the website’s greatest appeal, but also prove to be the most challenging elements for the conservation of the project. What are the limits of such variability and to what extent does its code and infrastructures change?
These two questions relate to another challenge: the time-consuming technical maintenance of the website. According to Neddam, because of the ongoing software updates and changes to the Web, she spends several hours a day fixing bugs and making small changes to mouchette.org’s code.14Although this may be overstated, and would certainly not be the case for every net artwork, the problem remains: What does this mean for the practice of conservation? How can such an involvement be implemented in existing workflows? More importantly, how much should a conservator know about a work? Knowledge is a necessary condition for authenticity. Various kinds of knowledge are involved in this case study, from material to art historical and social behaviours. In other words, in mouchette.org, nominal and expressive authenticity go hand in hand, and at times influence each other.
To summarize, mouchette.org is heterogeneous and continually re-negotiates its own conceptual structures. The development and maintenance involve incompatibilities, constraints, rules and a certain amount of improvisation. It poses several challenges for conservation. For instance, it consists of some old-fashioned material aesthetics; some of the outdated code and software can be difficult to read; maintenance can be very time consuming; participating users might change the work; and it evolves into other projects. It could be argued that these problems are not unique to mouchette.org, or net art for that matter; however, the combination is rarely found in other artforms.15 Moreover, the speed of developments, and consequently the depth and breadth of different knowledge fields, are major concerns. What knowledge and practical support is needed for a website to remain accessible?
(Re)constructing net art
The distinction between software and code is often blurred in common parlance, but understanding the difference between the terms often helps to identify authenticity. In general terms, software consists of the instructions that are entered into the memory of the computer, and is referred to as ‘soft’ because it is more malleable than the hardware (Petzold 2000). Software is the computer program that end users perceive and/or interact with, while code is what constructs that software; each software can consist of layers of code. Software and code are often hidden and not always directly visible. The hardware shields the programming and functionality beneath. Nevertheless, in most software the back-end code has a specific aesthetic that is easily recognized by those familiar with the programming language, and its ‘front-end’ aesthetics can also be discerned through historical comparison. Arguably, software itself does not have a specific aesthetic. Software aesthetics are largely adopted from other media and conventions. For example, desktop files and documents are clearly metaphors for office environments. However, computer functionality does produce distinct aesthetics, for example, low-tech aesthetics that, as explained by Goriunova and Shulgin, reveal themselves through the limitations of the technology:
Bottlenecks, such as processor speed, screen resolution, color depth, or network bandwidth – 4-bit, 8-bit music, 16-color pixelized visuals, slow rendering, compressed image and video with artifacts – create an authentic computer aesthetics, that is, the aesthetics of low-tech today.
(2008:113)16
Similarly, computer (hardware) displays also have certain aesthetics, mostly through their limitations; for example, screen resolutions, processor speeds and network bandwidth. A combination of these aesthetics, both hardware and software, can be traced in mouchette.org, which Neddam tries to conserve as much as possible to create a ‘witness’ to a specific time. The distinction between hardware and software can also be seen as the difference between front-end aesthetics and back-end aesthetics. The front-end is the Web browser, the interface of the website and the screen to view the work.
When opening mouchette.org, an immediate mid-1990s hardware and software aesthetic is recognized. The homepage shows a close-up of a flower covering two-thirds of the frame. The rest of the frame is tiled with the same image. The size of the larger image refers to the original width of a typical browser screen in 1996, with a resolution of 800 x 600 pixels (width x height). Similarly, the checkboxes next to the photo and the drop-down menu with the title ‘browse me’ at the bottom of the page signal the aesthetics of its language, HTML (HyperText Markup Language). In the early days of the Web HTML elements formed the building blocks of websites. The extensive use of these old features in mouchette.org can be seen as a longing for the past, a technical fetish. But to Neddam, there is more to it. By holding on to the old aesthetics and functions, she wants to highlight a time when the user controlled things more easily. As Neddam explains, the game of the ‘dead fly’ described earlier is a good example of how functions have changed and affected people’s behaviour. When she programmed the ‘dead fly’, visitors could resize the screen manually. It was not programmed to a fixed size, unlike some websites. Although the ‘it’s me’ button was extremely difficult to catch as it spun around the screen, the screen could be resized to make a small cage to trap it. This resizing also affected the Javascript program, which slowed down the movement of the button. Nowadays, resizing happens automatically, and since some sites protect their layouts, people tend to forget, or ignore, that it is possible. According to Neddam, this has led to a loss of user freedom and interaction.17 In a similar way, Neddam dramatized the limitations of long image loading times due to slow network connections. Short groans, howling dogs and a sobbing female voice played on repeat until the image was loaded. These could be adjusted with faster loading times, but the limitation of slowness and the repeating sounds proved good methods to heighten the tension of the narrative.
These aesthetic references are important elements that reveal aspects of the author’s creative process and artistic intent. Neddam works within the constraints of a past that bears witness to earlier Web aesthetics. She uses these early aesthetics to enforce this past. They also allow her to emphasize the theme of the website and its literary style. To put it more explicitly, just the idea that a 13-year-old made a bilingual and intricate website is already implausible. This narrative of misconception and false expectation runs through the website and is emphasized by hidden links and the deliberate (mis)use of tools. An example of the latter is the HTML checkboxes that lack customary functionality. Firstly, they are already checked, not to mention mere static graphic elements with text that links to other pages. As stated by art historian Matthias Weiss,
[t]hese are all hints towards the literary possibilities of the net, of moving within fictional trails within the texture of the Internet, and of inventing a separate and different identity. However, the site transcends the application of these and leads to a reflection of the mechanisms of self-construction.
(2009:170)18
Neddam is persistent in conserving the old aesthetics; however, this is not to say the website is static. On the contrary, mouchette.org is very dynamic, not only because external updates require the project to be adjusted, but visitors to the website also play an important role. They can comment on specific projects. They can also ‘be’ Mouchette by signing up to the Mouchette Network or by creating their own Mouchette page.19 Seemingly, these interactive elements make it easy to take control of mouchette.org. This use of commenting on issues and questions raised by Mouchette establishes the interactive side of the website. However, none of these actions influence the back-end: the software and code that is used. At first sight, the use of software seems limited to its functionality.
A functional use of software does not mean that software, or programming, can be easily migrated onto a new platform. For example, to make everything work properly after migration it would be easier, in theory, to rebuild mouchette.org in a PHP5 environment rather than adjusting the code in its current language (PHP4). Rewriting is easier than reworking existing software. Fixing outdated versions takes a lot of time and most programmers are not interested in, or capable of, doing this. Although the logic might be the same, the language of a new version may be different from the older versions. This is not to say the aesthetics, or the work itself, changes. Although they may, it primarily signals the existence of several parallel executions or reworkings of the artwork. Variations between versions are made in order to improve on or prolong the experience of the artwork. Moreover, even the best programmers forget exactly how older systems work. This is not necessarily a problem of remembering. Very simple programmes built two years ago might be difficult to fix, simply because the environment around them has changed. As mentioned by programmer Ellen Ullman:
By the time a computer system becomes old, no one completely understands it. A system made out of old junky technology becomes, paradoxically, precious. It is kept running but as if in a velvet box: open it carefully, just look, don’t touch.
The preciousness of an old system is axiomatic. The longer the system has been running, the greater the number of programmers who have worked on it, the less any person understands it. As years pass and untold numbers of programmer and analysts come and go, the system takes on a life of its own. It runs. That is its claim to existence: it does useful work. However badly, however buggy, however obsolete – it runs. And no one individual completely understands how. Its very functioning demands we stop treating it as some mechanism we’ve created like, say, a toaster, and start to recognize it as a being with a life of its own. We have little choice anyway: we no longer control it. We have two choices: respect it or kill it.
(2013[1997]:117)
So, it is not the memory of a single detail, but the whole ecology of both hardware and software that needs to be taken into account, as one minor detail is linked to or is dependent on another. This becomes clear in the following example.
As mentioned, Neddam is quite specific in her efforts to conserve the old software for as long as possible. However, instead of emulating or migrating old pieces to new software, she prefers to make the old ones function again by adding new patches to circumvent problems. For example, at the time they were made, some of the projects resulted from specific ideas, but the limitations in hardware formats prevented Neddam from realizing them. Neddam states that she created ‘Lullaby for a fly’, including its soothing and repetitive music, with the idea that one day a person would take a computer to bed.20 Although the possibility of taking computers to bed is very real now, Neddam’s feature runs on a specific version of Flash that does not function properly with current technology. Neddam thought of redoing the piece, emulating it. But, during the attempt, programming mistakes were made. The text would not run in the preferred order and eventually blocked the flow. Neddam accepted this at the time. And now, while considering the possibility of a new version, she is unsure whether to fix earlier mistakes or leave them as a record of earlier programming. As she explains:
I like that Mouchette’s back-end is a bit ‘dirty’. I like to compare programming to painting. Just as Mondriaan’s brushstrokes are very important, there is an authorial ‘hand’ to a website. All the compressions for example are on purpose. This hand speaks directly to the emotion and shows the intention of the work. I strongly believe that there’s a programming style which relates to the goal you want to reach.21
It could be argued that Neddam, in this case, prefers the material (nominal qualities) to her conceptual ideas (expressive qualities). However, taking into account the kind of materiality that I described in the introduction (i.e., highlighting technical and social relations of network culture from which materiality emerges), the relation between nominal and expressive qualities is more complicated, which makes a stringent division incongruous. While Neddam could not execute her initial concept due to technical limitations, these restrictions had a primary influence on her work.
To return to the importance of programming styles, computer programmer Paul Graham (2004) takes the comparison between painting and programming one step further. While advocating for their similarities, he suggests that hacking and painting involve the same creative process.22 Both of them are ‘learnt by doing’, meaning that most paintings have a history of sketches and consist of different layers on a canvas. These layers slowly lead to the final painting, in which every detail has been carefully chosen. Painters also copy and learn from existing works. Similar to literature, versions of paintings develop by copying the methods and styles of earlier masters, not necessarily in an attempt to make faithful reproductions. The artist wants to improve a skill and bring the history of painting (or literature) to new levels. A similar strategy can be found in open source practices, where one studies the source code and learns to program. In short, a painting evolves through sketches, layers and experimentation. Such a dynamic process is also visible in coding. This demonstrates why it is important to read the back-end of net art, not only to be able to restore the code, but to also see why and how certain decisions were made. As in the case of mouchette.org, technical limitations serve a conceptual goal. To quote Graham: ‘Great software, [like painting], requires a fanatical devotion to beauty. If you look inside good software, you find that parts no one is ever supposed to see are beautiful too’ (2004:29).
Personal programming is also a topic among programmers. Some even claim to recognize someone else’s training as, for example, originating from computer science or biology.23 Without moving into detail, the importance of human and cultural factors in programming, and thus computing, is demonstrated by the condition of ‘Turing completeness’. Named after Alan Turing, ‘Turing completeness’ signifies that a universal Turing machine can simulate every other computing device. This means that a machine, which acts as a universal Turing machine, can, in principle, perform any calculation that any other programmable computer is capable of.24 As researcher Florian Cramer points out, while machine functions might be interchangeable, ‘their different structures – semantic descriptors, grammar and style in which algorithms can be expressed – lend themselves not only to different problem sets, but also to different styles of thinking’ (2008:170). Similarly, media theorist Wendy Hui Kyong Chun shows that there are many myths around the dichotomy between the computer and its ‘all-powerful programmer who magically transforms words into things’ (2011:19).25She counters the belief that source code automatically does what it says. Such mystification of computing neglects the complexity of the execution. As she explains: ‘Code does not always or automatically does what it says, but it does so in a crafty, speculative manner in which meaning and action are both created’ (2011:24). This is to say that software is layered and shows itself most clearly in the execution of code. For instance, a programmer writes source code that consists of instructions in a certain language (for example, the commonly used C or FORTRAN).26 Computers can only execute instructions that are written in machine language (known as a low-level language). As such, compilers transform programs by producing intermediary forms or object codes that are similar to machine language. It may be that only lines of code that are necessary during particular moments or for specific programs may be executed (Chun 2011:24). Recalling Graham’s words earlier, source code can reveal more than what is executed.
This situation was demonstrated when programmer Mark Hellar looked into the work Agent Ruby (1999–2002) by Lynn Hershmann and found a 3D model and code that resembled a text-to-speech program. These were never used in Agent Ruby. As he describes: ‘It looked like they had been trying to create a 3D model that would convert text from the artificial intelligence program into speech, but that never happened’.27 This leads to the observation that not only do the writing styles differ, but also that the source code is not mere repetition. Some things are left out when the code compiles. Thus, the original source code may contain more information than what is seen after the compilation. In this case, the code could be said to contain contextual information about the technical constraints at the time, and possibly the artist’s ambitions (in 2004, Lynn Hershmann used a text-into-speech system in her project DiNA).28 It is important to understand source code as something ambiguous and not as generalized writing. As Chun also argues, when dealing with computer languages it is a myth to think that there are no mis-readings or misunderstandings and only transparent information (2011:79). The extent to which code is ambiguous, and hence what can or cannot be altered, is crucial to the practice of conservation, particularly when considering which approach to take in re-creating or conserving a work. Furthermore, if software is the behaviour of the machine or a process in action, then how can a historically significant compiler, operating system or database be conserved?
To briefly summarize, so far I have emphasized the following points in identifying the relevancy of authenticity in software-based art. Firstly, conceptual ideas are influenced by the restrictions of hardware and software, but these limitations can become driving forces. Secondly, the act of programming, programmers and the code are part of an artwork’s style and aesthetics. Thirdly, code often contains contextual information that is not necessarily used, but can clarify as well as cloud meaning. I will explore the relevance of these points in more detail in the following by analyzing a media-archaeological reconstruction of the computer-based artwork LoveLetters by David Link, and compare it to Neddam’s endeavours.